$10 to Access Machine at an International Airport
페이지 정보
작성자 Anna 댓글 0건 조회 150회 작성일 25-02-05 13:46본문
One other method identified was utilizing a professional shipping label but obfuscating the related information on the label that might identify the person or the order information. It's necessary to mint the Black Pass with a purpose to earn the shards. Finishing the demo will earn you the utmost shards in a single quest. That can assist you get began in your journey, Astra Nova will provide all customers with 20 free transactions so you'll be able to replace your shards count. Problem two was, blackpass.bz if it does drop down on focus, are you able to pull it back up indirectly? So that’s a method you could overcome not having a management for it to pop back up, and that i do encourage you to use the escape key to make that pop back up, however arrow key navigation, pretty useful, so it allows them to tab into it, and then transfer the main target round with arrow keys, however to try this, you’re going to have to add a keypress Event Listeners to no matter has focused, the menu merchandise that has centered, and when it hears the best arrow key, it’s going to move the focus to whichever merchandise that you really want, which is probably going to be this next main predominant menu merchandise.
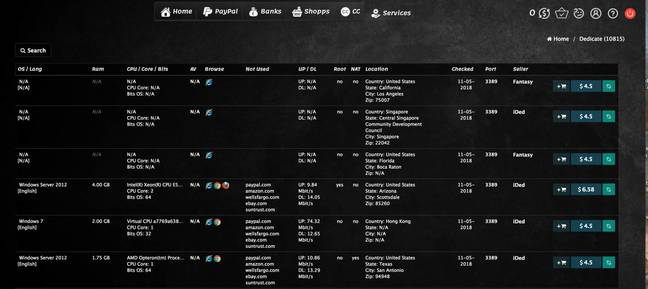 DENEB: cache https blackpass.bz Sure, and you probably did, too, you already know, you mentioned you code the escape so that it just pulls the menu back up, which is a good solution to do it. They’d hear, "Link, African-American History, collapsed," and by hearing that phrase collapsed, they might know, "Oh, it’s collapsed proper now. I’ve acquired a page of a website that helps folks sort of find out how to make use of screeners somewhat bit and apply it, and so if you’re looking to get into screen-reader testing, I say soar into it, and use Voiceover or use NVDA to just do this, you already know, is it saying collapse? Voiceover shouldn't be always clear because it does barely various things relying on what browser I take advantage of," and that is Emily for the attention. The majority of these credentials had been harvested utilizing both Redline, Vidar or Raccoon malware. Given the latest rise in popularity in malware related cryptocurrencies and exchanges, it might solely be a matter of time when such malware turns into probably the most bought and bought commodity on such marketplaces. Having the primary menu item solely as an action trigger for the dropdown is likely to be a superior approach, because it clears any confusion about whether clicking it would lead to a unique web page or simply open the submenu.
DENEB: cache https blackpass.bz Sure, and you probably did, too, you already know, you mentioned you code the escape so that it just pulls the menu back up, which is a good solution to do it. They’d hear, "Link, African-American History, collapsed," and by hearing that phrase collapsed, they might know, "Oh, it’s collapsed proper now. I’ve acquired a page of a website that helps folks sort of find out how to make use of screeners somewhat bit and apply it, and so if you’re looking to get into screen-reader testing, I say soar into it, and use Voiceover or use NVDA to just do this, you already know, is it saying collapse? Voiceover shouldn't be always clear because it does barely various things relying on what browser I take advantage of," and that is Emily for the attention. The majority of these credentials had been harvested utilizing both Redline, Vidar or Raccoon malware. Given the latest rise in popularity in malware related cryptocurrencies and exchanges, it might solely be a matter of time when such malware turns into probably the most bought and bought commodity on such marketplaces. Having the primary menu item solely as an action trigger for the dropdown is likely to be a superior approach, because it clears any confusion about whether clicking it would lead to a unique web page or simply open the submenu.
It’s already set up, and so that you don’t suppose much about it, but when your visitors come in to your site, in case your menu doesn’t work for them, they're kind of like this individual here on this canoe. The airport is unsure how the credentials acquired out, but McAfee analysts think a brute-power approach was likely used to "guess" the login data. In concept, yes. But when we predict realistically, such an assumption would appear unlikely because DNStats retains working. DENEB: Sure. Sure, completely, so it’s form of a separate concern than the ones we’ve been discussing, and that’s something that I realize is a failure of my presentation. We’ll discuss Mega Menus more with the following questions in all probability, however sometimes within Mega Menus, there might be, like, form of headings inside that Mega Menu, and those may have Aria-stage of two or three or whatever it must be, however then, most likely, www.blackpass.bz best observe would be to not let those be links themselves, as a result of then that might change the semantics. It factors out that a part of the problem is corporations have been gradual to undertake two-issue authentication --- a measure that would thwart this sort of breach.
Airport officials confirmed the validity of the login info after being notified and have since resolved the breach. It is possible that threat actors were making an attempt to make the most of the holidays with workers probably being out of workplace. Malicious menace actors discerned faux tracking ID (FTID) methods that work for particular merchants and traded that data. Generally, threat actors requested mail-in refunds following costly purchases, and they returned a package deal with the proper label however would not put the suitable merchandise in the box. Adrianne has mentioned: "If they sometimes set the primary item to href anchor, however that’s an accessibility error, how can that be answered? Contemplating the supposed use, we observed the retail sector’s buyer base and retail organizations’ executive staff as the primary victims of information posted available on the market. ’ effects on our current customer base. It uses RDP to allow workers to access particular techniques from exterior the LAN.
댓글목록
등록된 댓글이 없습니다.
